[vc_row][vc_column][vc_column_text]People have always topped the list of what keeps enterprise executives up at night. Leaders wonder, “Is the right talent in the right places?” and “How do we maximize employee productivity and improve our customer experience?” Now two years into the pandemic, executives have a new people-related concern, “How do we stop bad actors from compromising our data and stealing it for gain?”
Nearly nine in ten C-suite and other executives (87%) recently surveyed expect the number of cyberattacks targeting their organizations to increase over the next 12 months, reports Deloitte. And while almost two-thirds (65%) believe ransomware poses a major concern to their organization, only a third (33%) say they have prepared for such attacks.
That’s not surprising considering how fast the vectors and targets of attacks are changing. The market saw a 1,070% increase in ransomware between July 2020 and June of 2021, according to a semiannual Global Threat Landscape Report.
How can enterprise executives turn the tide, quickly pivoting from chasing to detecting and mitigating both external and insider threats? A giant first step is to rethink legacy data management infrastructure and architecture. Here’s why.
Legacy Data Management Hinders Cyber Hunting
Legacy infrastructure is complex and closed. An organization can have multiple silos, vendors, and fragmented data, leading to inefficiencies in processes, management, and systems designed to uncover threats. That makes it easier for criminals to get in and begin encrypting data for a quick payday (ransomware 1.0).
Moreover, legacy infrastructure is vulnerable. Requirements for specialists to manage each silo individually and inconsistent patching and other protection processes are weak-link targets for hackers to enter the environment and not only encrypt data, but destroy backups to make data recovery more difficult (ransomware 2.0).
Lack of intelligence in a data management solution is another flag to bad actors that enterprise data is not well protected. If IT teams have to spend hours or days manually sifting through logs to discover intrusions, attackers can penetrate and run malicious code inside of an environment for a long time before encrypting data, compromising backups, and stealing the data for maximum ill-gotten gains and reputational damage (ransomware 3.0).
Although IT modernization is on enterprise executives’ minds, most are just beginning to recognize the important link between eliminating legacy data management and bolstering threat defenses. That’s where the Cohesity Threat Defense architecture and Cohesity and HPE solutions come in.
By embracing an architecture and solutions focused on not only data security but on cyber resilience, organizations can better defend their data in the hybrid and multicloud era.
Architecting for Cyber Resiliency
Threat Defense is a defense-in-depth architecture to counter cyber threats that goes beyond Zero Trust security principles to keep data and applications secure. It helps keep bad actors away with least-privilege methods and advanced access controls while learning and continuously monitoring data changes using artificial intelligence and machine learning (AI/ML) techniques. It also serves as a framework for other security solution integrations. Comprehensive and multilayered, the Threat Defense architecture more closely aligns InfoSecOps professionals and teams, improving security postures.
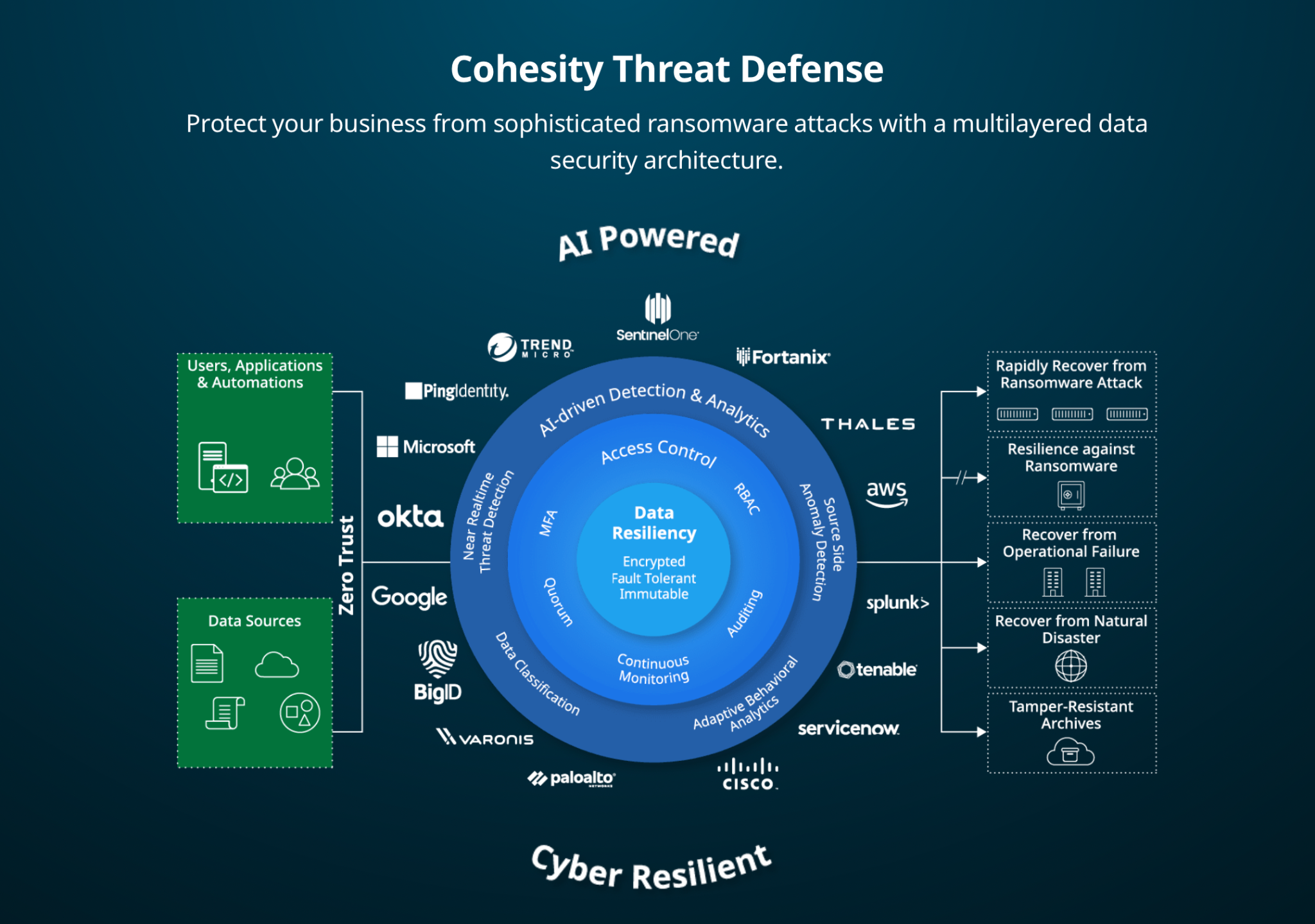
Figure 1. Comprehensive Threat Defense Architecture from Cohesity is Key to Cyber Resilience
Key capabilities of the Threat Defense architecture, brought to life in Cohesity and HPE solutions, include:
- Data resiliency – At its core (as illustrated in Figure 1), Threat Defense is about providing organizations with a highly resilient platform that helps ensures confidentiality, availability and integrity of data. Key to safeguarding data is Zero Trust security principles, encryption, WORM (write one, read many) techniques, fault tolerance, and immutable snapshots. The latter ensures backups cannot be modified or deleted, thwarting ransomware 2.0 attackers.
- Data access – Policy-based controls within the architecture platform help prevent unauthorized access to sensitive data no matter where it resides—core, cloud or in edge locations. From role-based access (RBAC) and multi-factor authentication (MFA) to requiring more than one person to make root-level changes and continuous monitoring and auditing, Threat Defense helps ensure resilience for the data collected today as well as tomorrow.
- AI-driven insights – Another important architectural component to stopping threats is detection and analytics. These include data classification or cataloging what data is there and near real time anomaly detection or continually assessing the data to recognize and alert teams when patterns change, which can signal a ransomware attack. These capabilities give data security teams confidence they know where sensitive data resides and governance and compliance teams knowledge about who’s accessing it.
- Security features/apps extensibility – No single security product alone will be able to thwart all threats. That’s why the architecture platform features both integrated apps and APIs including vulnerability scanning, data masking and more that empower teams to join forces in combating bad actors.
Threat Defense is designed for real-world environments, which means it’s architected to recover in a worst-case scenario ransomware attack or operational failure as well as failover gracefully in the event of a natural disaster. The platform supports the instant mass restore of hundreds, even thousands, of virtual machines (VMs), databases and more to the date and time of the last-known clean copy, providing confidence infected data isn’t reintroduced into the environment.
Getting Executives a Better Night’s Sleep
Cohesity and HPE at the foundation of Threat Defense architecture can help put enterprise executives’ minds at ease. They can be confident that a modern data management platform is keeping sensitive data protected and unplanned downtime to nearly zero.
They also can be assured they have automated safeguards in place against human errors, natural disasters, and cybercriminals—but just in case, that their teams have the ability to recover data fast and with confidence that it’s free of ransomware. Moreover, jointly delivered Cohesity and HPE solutions empower organizations to reduce compliance risks and protect business reputations by preventing data downtime and breaches.
Are you ready to defend your organization’s data against ransomware? Access this guide to find out.
Discover Cohesity–HPE Solutions for Cyber Resiliency
Together, Cohesity and HPE deliver integrated data protection and data management solutions that eliminate silos so you can easily back up, access and extract insights from data. Best-of-breed solutions, spanning on-premises, cloud, and the edge, combine the simplicity and efficiency of Cohesity data management software with the power and density of industry-leading, certified HPE Apollo and HPE ProLiant servers and can be delivered as a service through HPE GreenLake, hybrid cloud, or self-managed.
Learn more about Cohesity and HPE.[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column width=”1/4″][vc_single_image image=”7119″][/vc_column][vc_column width=”3/4″][vc_column_text]
Joanna Paul
Senior Solutions Marketing Manager, Cohesity
Seattle, WA, USA
Joanna Paul leads the Cohesity | HPE Solution Marketing efforts for Cohesity. A seasoned technology marketing professional, Joanna is passionate about providing compelling value propositions and creating high value content.
LinkedIn[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][vc_empty_space][/vc_column][/vc_row]



