Hewlett Packard Enterprise is known for its enterprise solutions in the storage ecosystem to effectively store customer data and provide all the mechanisms to protect the data it stores. There are too many attack vectors that can lead to a successful compromise, if not protected against. One of the most important and proven methods to protect internal and external data from falling into the wrong hands is encryption. Almost all solutions offered by HPE offer encryption natively to safeguard customer data.
Apart from safeguarding customer data by leveraging encryption, there are many regulatory compliance bodies including PCI, HIPPA, SOX, GDPR, etc. that mandate encryption as one of the most important and non-negotiable control measures.
In light of all these industry best practices and enforcement from regulatory bodies, encryption is now accepted as the de facto strategy for protecting all sensitive data. But with this ease of safeguarding the customer data, comes some complexities.
Encryption moves the responsibility of safeguarding the data to a reduced number of core factors and if not done correctly can result in a denial of service or compromise and hefty penalties with a loss of revenue.
What can go wrong!
There are many outside (and inside) threats to your data. Hacking, phishing, malware, ransomware, data leakage, and cloud computing, just to name a few. Nowadays though, attackers have become more and more sophisticated, which means that the protection methods need to evolve in order to stay ahead of these threats.
Encryption will protect your data, right? The answer to that question is not a simple yes or no, but relies on a well-established security posture and set of practices which the organization needs to adhere. Encryption is based around secure algorithms which require secure key management to protect the data which in turn raises some critical questions that need to be addressed –
- Who has gained access to the keys?
- Where are the keys stored?
- Are they safeguarded against prying eyes?
- Am I using a unique key for each asset protected or are they being reused?
- Is the access to the keys audited?
- Do we have separation of duties and keys when stored?
The Key to Enterprise Data Security
The end goal is to ensure that “the right key is made available to the right asset at the right time and log the usage”. To make this a seamless process, ensuring that there is a dedicated entity to manage the encryption keys is a necessity. These requirements bring in the concept of key-manager – a dedicated, certified, secure, audit-controlled appliance that gives you the right peace of mind while protecting the keys to your kingdom.
Key management usage continues to rise
Enterprises have realized the need for key management and the market was valued at $1,451 million in 2020 and is now expected to reach $5,456 million by 2026, at a CAGR of 20.7%. (Source: Globenewswire.com).
The volume of data created, used, and stored worldwide is expected to grow to 181 Zettabytes by 2025 which means an increase of approx. 129% in comparison to the volume of data in 2021. And it’s needless to say – this data needs the right protection.
Also, with the adaptation of cloud, the data is no longer confined to the boundaries of an organization but is going places. Nobody knows when you place your data in a public cloud, where it lives, or a way to control it. Almost all the Cloud Service Providers (CSP) are coming up with different techniques to offer data encryption while the customers are still in charge of the keys. For example –
- Microsoft Double Key Encryption
- Google External Key Manager integration
- BYOK supported by almost all CSPs
Let’s assume that an organization has done a good job in protecting itself against threats and is using key management. Even with key management in place, should a key become compromised, the organization may never know it until it has been exploited by the attacker. Weak keys, incorrect use of keys, non-rotation of keys, and inappropriate storage of keys, are just a few of the challenges organizations face even with key management.
The answer then is to mitigate these underlying threats with secure and sophisticated key management.
What does a key management solution look like?
As enterprises today use thousands, and even millions of encryption keys and the storage of these keys becomes more and more tricky, the number one challenge that a key manager should solve is to provide a centralized storage solution for these keys. Other than storage, it should also provide the highest level of security – tamper responsiveness, and industry certifications like FIPS. It should also meet audit, compliance, and other regional mandates. It should use automation to generate keys, renew, and rotate them. As not all employees need access to the keys, the key manager should provide role-based access to keys. All of these features are included in a low-maintenance, simple-to-adopt solution.
The vast majority of enterprises are now employing a multi-vendor strategy hence the key manager of choice needs to be able to integrate with all relevant vendors, making interoperability essential. As the organization grows, the key manager needs to be scalable, and highly available to avoid a single point of failure.
With the adaptation of cloud, another consideration is a multi-cloud key manager that can safeguard keys when deployed in the cloud but provides an option to integrate with a centralized root-of-trust Hardware Security Module (HSM) which can be placed on-prem or in the cloud.
How does Utimaco’s ESKM add value to HPE’s data storage solutions?
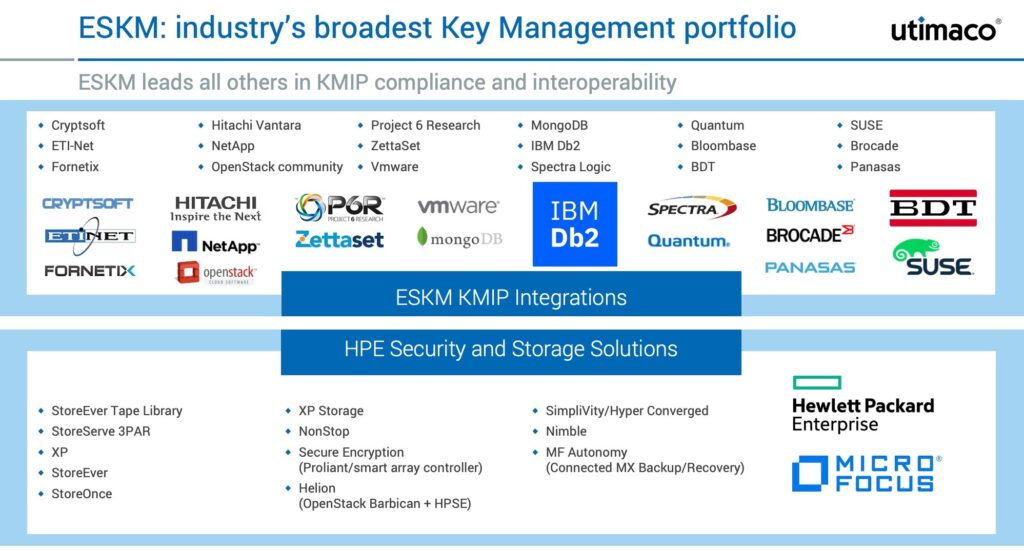
Traditionally being a part of HP/E’s storge ecosystem, Utimaco Enterprise Secure Key Manager (ESKM) appliance is a complete solution for generating, storing, serving, controlling, and auditing access to data encryption keys. ESKM is the key manager of choice and integrates with the entire HPE ecosystem, in a nutshell, wherever HPE stores and encrypts the data, ESKM helps to safeguard the underlying business-critical and sensitive encryption keys. ESKM is:
 Secure
Secure
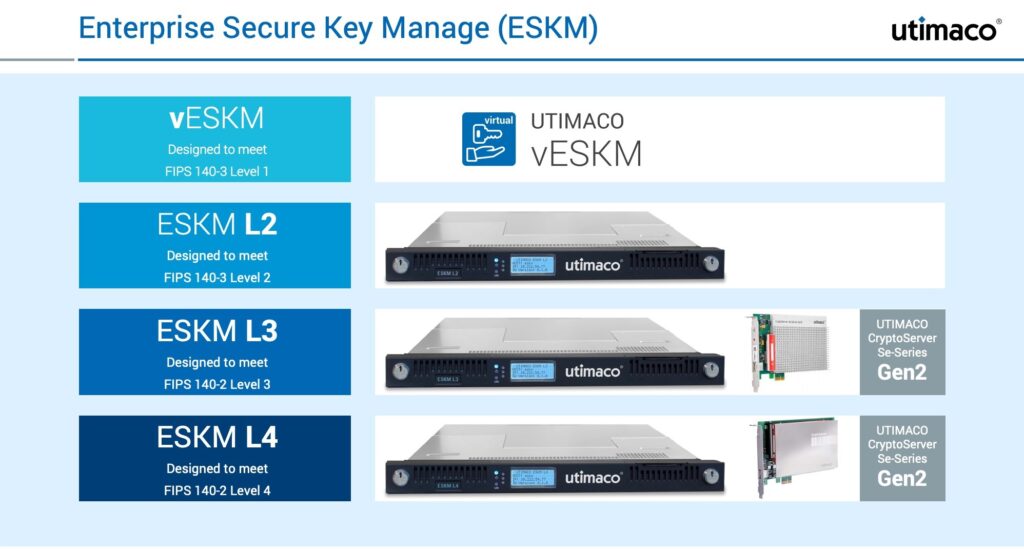
- Meets NIST standards and allows protection at all Levels of Federal Information Processing Standard – 140-2 (Level 1, 2, 3 & even Level 4)
- Encrypts keys in transit and at rest
- Certificate-based authentication and built-in CA
Manageable
- Configuration and keys replicated across cluster automatically
- Hands-off administration, automated backups, and audit logging
- Deploys as a Virtual Machine or Physical Appliance
- Integrates with Utimaco CryptoServer as a root-of-trust
Available
- Scales with thousands of nodes in an Active-Active cluster
- Automatic key replication, client failover
- Highly redundant hardware
Scalable
- Geographically separated clusters across datacenters
- Supports thousands of clients, and millions of keys
Interoperable
- Supports OASIS KMIP (Key Management Interoperability Protocol)
- HPE native KMS protocol
- REST API for Key management and crypto operations
- No vendor lock-in
- Custom integrations using SDK
All these benefits are available across the board, irrespective of the storage in use or even when using non-HPE assets like VMware for virtualization or MySQL to store your data. A right key manager must offer the broadest integration portfolio and Utimaco ESKM leads the space with its integrations in the storage space.
Conclusion
HPE provides robust data storage and compute platforms to store enterprise data and Utimaco ESKM stands with HPE to safeguard these assets while protecting the encryption keys in a secure and FIPS 140-2 compliant fashion.
Visit our website to learn more about the most interoperable and integrated Key Manager in the market.