New approaches to innovative security architectures are starting to emerge, including HPE’s groundbreaking Project Aurora. Here’s how to make zero trust architecture work for your business.
 The broad concept of zero trust architecture has achieved wide acceptance in the marketplace, but exactly what it entails has been a subject of debate and even some confusion.
The broad concept of zero trust architecture has achieved wide acceptance in the marketplace, but exactly what it entails has been a subject of debate and even some confusion.
Fortunately, we’re moving beyond that now. Some government bodies, like NIST, have published papers that lay out exactly what zero trust is all about.1 That guidance is important when you’re casting such a wide net in the realm of cyber security. Using a common terminology can help companies avoid the situation where you’re talking to one vendor and thinking and hearing one thing – and then when you talk to another vendor, you’re hearing something else. That’s the kind of disconnect that new definitions and guidelines can help you avoid.
That said, it’s important to realize that zero trust is not a one-size-fits-all solution. We’re now at the point where we can, for example, create maturity models for it (HPE has one.) But those models can and should be adapted to your unique scenario. Think of zero-trust as a kind of continuous guiding light. You’re always looking to monitor, you’re always looking to secure the communications, you’re continually authenticating and validating. The basic core tenets of zero trust should be structured into every project that the organization takes on, while balancing against your risk appetite. But it’s not an end state; it’s something that will continue to change as security technologies evolve.
4 key moves for zero-trust security
Zero trust isn’t a one-size-fits-all, and it’s not a one-time deal either. There are some key aspects that you should measure yourself against along the way.
1. Know the terrain. Job one is to really understand your security landscape. What is your attack surface? Does it include IoT/OT? What are the ‘crown jewels’ of your IT assets? What do you most need to protect? These are all basic elements of cybersecurity strategy, but they may take on a somewhat different color when seen in the light of zero trust. NIST offers this principle – ‘all data sources and computing services are considered as resources’ – as one of its seven key tenets of zero trust.
Another tenet is continually monitoring communications for abnormalities – a session-by-session validation of communications. For example, let’s say your PC is talking to one server, but then all of a sudden it starts talking to a thousand servers? Seems odd, to say the least, right? So we look for abnormalities on a continual basis.
Another part of knowing your terrain, one that’s not talked about as much, is testing. Validate that the controls you have put in place are working and current against the latest threat landscape.
2. Balance recommended practices against your specific needs. For example, if you have properly encrypted and secured each of the individual devices within a secure location, then do you really need to encrypt everything on that local area network? For many organizations that’s not realistic. Encrypting absolutely everything going off from a laptop, for example, would create a very heavy load and a drag on performance.
So you have to find the right balance. Inside the data center, you might want to start encrypting everything there – it’s difficult, but it’s becoming more feasible with technologies like smart NICs (see my post The New Edge Is Here: The Tectonic Shift Needed for Workload Connectivity). Apply this concept across all of the NIST tenets – balance the benefits of achieving the objective vs the cost and complexity of getting there and operating the solution going forward.
3. Take a step-by-step approach. What are your weakest points right now? What are your biggest risk concerns? What appetite does the business have for this risk? You may be able to apply some zero trust principles right now to fortify those specific gaps. Identify a maturity model, know where you are, and then determine the right steps to address things that fall outside of your risk appetite.
4. Tie it back to the business. The ultimate litmus test of success with zero trust is its ability to align with business priorities. You’ll want to show that IT is rowing in the same direction and be ready to explain – i.e., show the metrics on how zero trust delivers crucial benefits.
Today’s risk register may tell you that you have important data siting at remote locations on old workstations, old Microsoft Windows instances. Applying some zero trust principles could probably help. But the business might have other priorities in mind. Maybe what’s top of mind for management is six M&A moves coming up in the next year, and it all has to be done in a secure fashion, along with absorbing all the IP and everything else that goes with that. Knowing the organization’s overarching goals is crucial.
Security is primarily a metrics-based exercise – even with the current ransomware wave and other attacks that are always going on. It’s not enough to report that “we stopped a thousand malware events today.” The response might be: “Well, that’s great. But how many did you let through? How many were there in total? And how do we quantify that risk to the business?”
Or let’s say you want to report that you stopped a DDoS attack today. Okay, great – but, from the business’s point of view, isn’t that what you should be doing day-in-day-out? Be prepared to unpack the details: “The defense was actually done a very unique way, the attack was aimed against a part of the business that could have been put at risk, and it could have cost us $50 million.”
You don’t have to go at it alone
Use these four principles as checkpoints for the journey. Keep them in mind for major decisions along the way. And bear in mind that if internal security expertise is in short supply, you can leverage industry experts like HPE for anything from filling immediate gaps to building your maturity model.
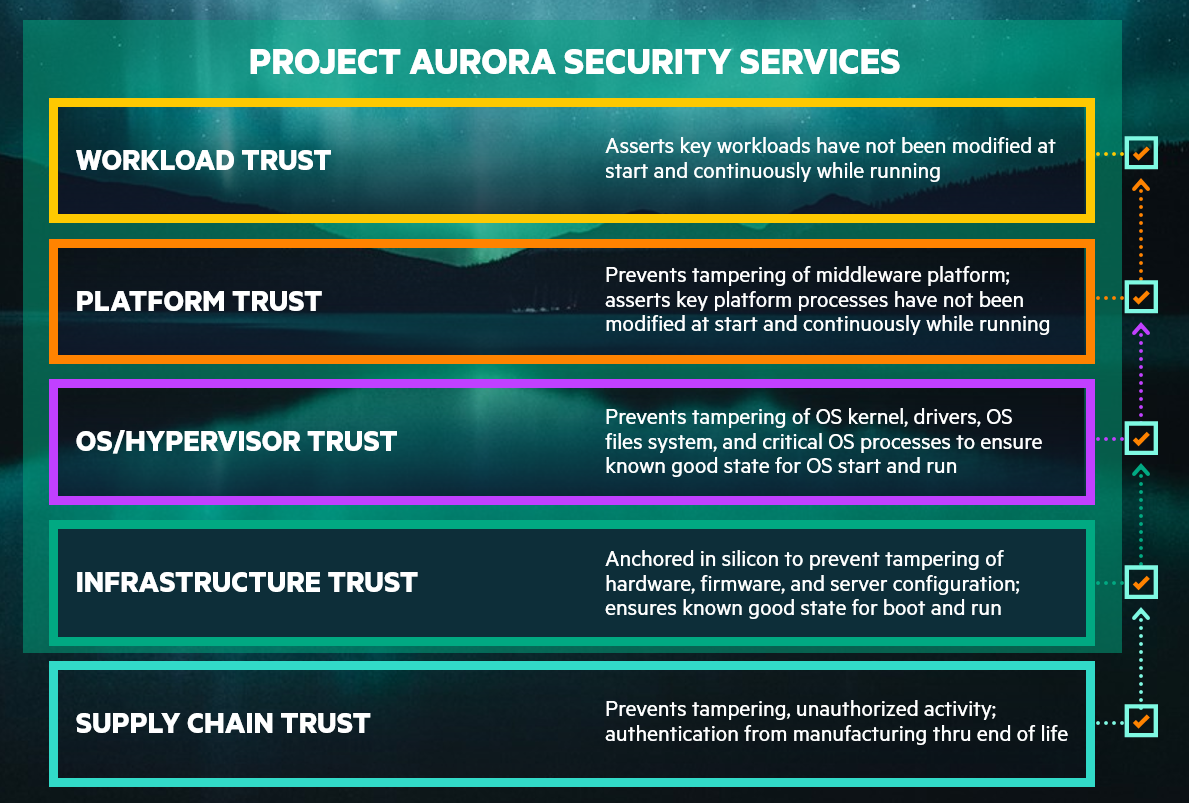
HPE has a long history of expertise and innovation in security. You might want to investigate Project Aurora, HPE’s comprehensive framework that will deliver cloud-native, zero-trust security for HPE GreenLake edge-to-cloud platform. Project Aurora is an embedded security platform that continuously and automatically protects without signatures, significant performance trade-offs, or lock-in.
HPE has long held a leadership position in server infrastructure security solutions, with our silicon root of trust architecture. Project Aurora will extend that architecture very broadly – it will encompass everything: operating systems, software platforms and workloads.
HPE: a leader in Network Consulting Services
Per IDC analysis and customer feedback, HPE is also positioned as a Leader in the 2021 worldwide IDC MarketScape on network consulting services. Read an excerpt from the IDC Marketscape: Worldwide Network Consulting Services 2021 Vendor Assessment

IDC MarketScape vendor analysis model is designed to provide an overview of the competitive fitness of ICT suppliers in a given market. The research methodology utilizes a rigorous scoring methodology based on both qualitative and quantitative criteria that results in a single graphical illustration of each vendor’s position within a given market. The Capabilities score measures vendor product, go-to-market and business execution in the short-term. The Strategy score measures alignment of vendor strategies with customer requirements in a 3-5-year timeframe. Vendor market share is represented by the size of the icons.
HPE can help you on every step of your journey to zero-trust security. Our Network, Digital Workplace and IoT Edge Technology Services enable you to optimize connectivity and create secure, uninterrupted network access across your enterprise and workloads, supporting all devices across your digital workplace.
Learn more about HPE Pointnext Services.



