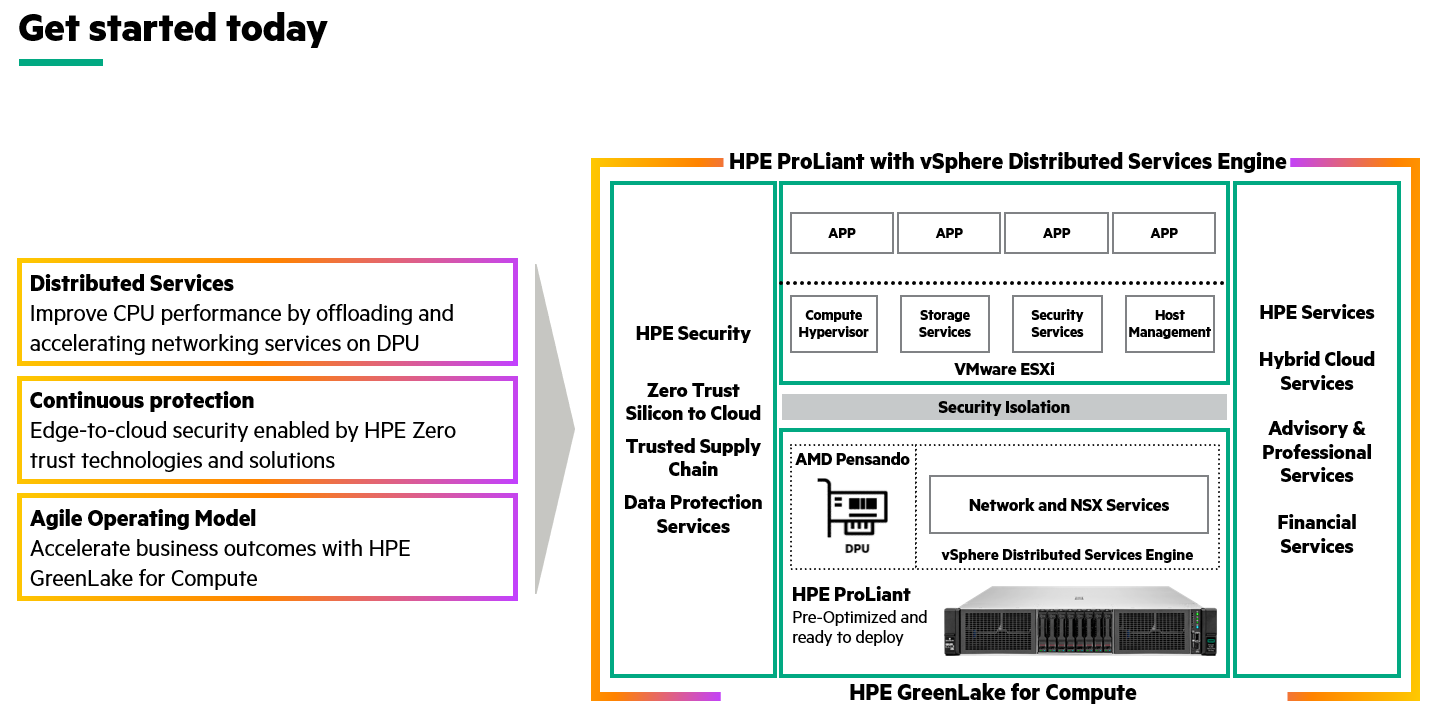
Today we are excited to announce the new HPE ProLiant with VMware vSphere® Distributed Services Engine™ developed in collaboration with VMware and AMD Pensando as the first HPE solution for VMware’s Project Monterey. This new solution enables the data processing unit (DPU) to offload services from core processors and improve application performance with a modern distributed architecture.
“Together with VMware and AMD Pensando, HPE continues to define the enterprise architecture of the next decade. The HPE ProLiant with vSphere Distributed Services Engine optimizes resources for data-intensive applications by relieving the CPU of networking services, all with zero-trust security and high performance. The new integrated solution offers customers a simplified operational experience combining networking, security, storage, management, and lifecycle services to boost application performance and improve TCO.” Krista Satterthwaite, HPE Senior Vice President and General Manager, HPE Mainstream Compute
VMware’s Project Monterey is an industry initiative, first announced in 2020, that addresses the complexity and demands of modern workloads that Enterprises face today. These increased demands are due, in part, to the advent of software-defined infrastructure services – or microservices – that add to the load on CPUs.
Research shows that up to 78% of CPU cycles are used by infrastructure services today – which could be better spent on applications that drive greater business value. So, the impact is clear: more services running on the CPU mean less CPU cycles for customer workload applications. This increased usage affects not just performance; it also compromises workload consolidation and ultimately increases the total cost of ownership.
“The new HPE ProLiant powered by vSphere 8 with vSphere Distributed Services Engine will enable customers to modernize cloud infrastructure into a distributed architecture enabled by DPUs,” says Krish Prasad, Senior Vice President and General Manager, VMware Cloud Platform Business. “Customers will be able to deliver better infrastructure price-performance by providing more CPU resources to workloads, while meeting the throughput and latency needs of modern distributed workloads by accelerating networking functions.”
Security issues continue to loom large for Enterprises
Much like the GPU, the DPU is also an accelerator, but it is specifically designed for management services such as security, storage, and networking. Security continues to be a major concern for many. Only 35% of organizations were confident that they could prevent a persistent security threat, and they highlighted this capability as a key requirement for evaluating any new solution.
While the initial release of the HPE ProLiant with VMware vSphere Distributed Services Engine will enable the offload of networking services, the potential benefits are compelling. In the future – beyond today’s virtualized and containerized workloads – the DPU can also act as a control fabric to enable more types of workloads, such as bare metal and security enhancements that isolate infrastructure services from the workload domain.
Evolving legacy IT architecture that takes advantage of technological advances can get complicated quickly, slowing implementation. That’s why HPE GreenLake is the perfect way for customers to deliver the business value of Project Monterey, most rapidly, with an 80% faster time to market.
What does the HPE ProLiant with VMware vSphere Distributed Services Engine deliver?
HPE ProLiant with vSphere Distributed Services Engine utilizes the HPE ProLiant Gen10 Plus server as the fast, flexible compute foundation that is highly suited for modern workloads. It features a scalable subsystem, large memory footprint, and is the world’s most secure industry-standard server.
For the DPU, HPE partnered with AMD Pensando. As an early partner, our combined global team had extensive experience in both designing and deploying solutions – with thousands of DPUs – in environments of all sizes, as well as multiple industries.
Here’s a rundown of the key benefits:
- Performance boosted for virtualized workloads through acceleration with distributed infrastructure services
- Offload NSX networking & native vSphere networking services from CPU to DPU.
- New VMware vSphere8 supports the installation of ESXi on both DPU and CPU.
- Simplify operations of DPU lifecycle management by utilizing existing tools and workflows.
- Accelerated business outcomes faster with HPE GreenLake for Compute
- Scale up or down, on-demand, to meet unexpected business needs.
- Pay-per-use solution with visibility into near-real-time consumption and cost.
- Reduce your total cost of ownership and eliminate the need for expensive overprovisioning.
- End-to-end protection, from silicon to cloud, plus Zero Trust with the world’s most secure industry-standard server
- Uncompromised, trusted supply chain, acting as your first line of defense against cyber-attackers.
- Protect against ransomware with fast, reliable recovery and backup, with cost-effective archiving featuring HPE data protection solutions.
Worldwide financial, professional, and advisory services
To help accelerate your plans, HPE Services and our global partner network are ready to help. From removing funding barriers to acquiring new technology to doing more with your budget, HPE Financial Services enables you to proactively prepare for modernization and expansion. To augment your in-house expertise or to help manage your team’s workload, HPE Advisory and Professional Services can assist every step of the way – from design to deployment and beyond.
Want to learn more?
To learn more about this exciting announcement from HPE and VMware, please check out our VMware Explore 2022 on-demand session, Next Generation Infrastructure with HPE and VMware Project Monterey, Session ID: 1538. You can also read the press release and VMware blog.
And – check out our website and be on the lookout for upcoming availability announcements. We’ll be providing more detailed ordering information on our pre-optimized solutions as they become available.