[vc_row][vc_column][vc_column_text]
The latest ransomware attack on the market was a doozy. Just a few weeks ago, the Russian hacking group known as REvil attacked MSPs (Managed Service Providers) that utilize Kesaya’s VSA software, holding them hostage for a total ransom of $70M. The cyberattack affected 800 and 1,500 organizations, disrupting IT functions for MSPs and their customers around the world. The impacted ranged from a grocery store in Sweden to a school district in Australia, and all points in between.
With the recent hyper-focus on ransomware from the US media, it’s worth taking a little deeper look at the current cyber environment and the best practices organizations can employ to mitigate these cyber threats.
These attacks are nothing new
With so much focus on the latest stream of attacks in 2021 (Solar Winds, Colonial Pipeline, JBS Meatpacking), it is easy to forget that bad actors have been stealing data for a very long time. Remember the theft of over 45 million credit card numbers from retail giant TJX back in 2006? How about the cyberattack against US military bases in the Middle East back in 2008? Does the 2013 Target breach, in which 40 million customers’ credit card numbers were stolen, ring a bell? Then there were the two attacks on the US Office of Personnel Management attacks where 22 million personal files were stolen (including social security numbers). The extent of this attack was not even realized until a year later. Finally, the attack on shipping giant Maersk in 2017 cost the company over $300M and took over two weeks to recover fully.
These are just a few of the more notable attacks in the somewhat recent past. The reality is, for each of these attacks I cited, there have been thousands more. And while the direct costs have been in the billions of dollars, the downstream cost to consumers has been far too steep to measure.
The attack vectors (or ways) these bad actors gain access varies. With the explosion of connected IoT devices and the corresponding rise of edge computing, the number of devices and types of infrastructure (attack surfaces) is increasing exponentially. The data generated on the devices at the edge makes these targets high value.
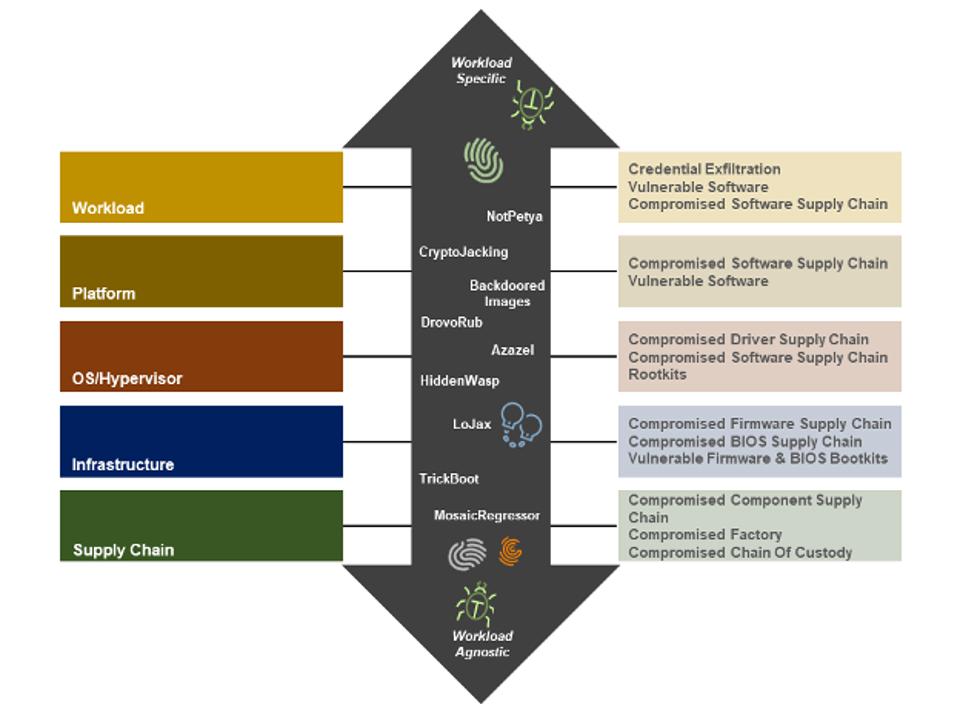
Finally, the attacks continue to increase in sophistication. While enough jokes have been made of the Nigerian Prince trying to recapture his fortunes, the complexity of today’s attacks can cause such exploits to go undetected for a long time. According to FireEye-Mandiant research, the average ransomware attack lasts 24 days. And more sophisticated attacks targeted at exfiltrating data last on average of 207 days per IBM-sponsored research. The methods by which these cyberattacks happen vary, but the results are the same – substantial financial losses and damaged reputations.
Zero trust needs to be given
If the above doesn’t articulate the need for an IT security strategy and practice built on zero-trust, stop reading. However, if this resonates (as it should), make the investments in a zero-trust strategy that includes the three Ps: people, process and product (technology).
A comprehensive zero trust strategy must account for the entire data environment – from the core data center to the edge and the cloud. Further, zero trust must account for the entire stack – from the time infrastructure is deployed to boot sequence to the workloads and applications that generate and utilize data.
A real cybersecurity strategy begins before infrastructure is deployed
Depth of defense is essential. And depth of defense applies to infrastructure on a couple of planes. The first plane is absolute protection of the operating environment as soon as the power button is depressed – that is, before the OS and applications load. By scanning a server’s 5 million or so lines of pre-boot code and files, rootkits, bootkits, spoofed firmware and more, the attacks are detected and resolved.
The other defense plane applies to ensuring the security of infrastructure throughout its lifecycle. Meaning, ensuring the components that populate a server are authentic and free of tampering – from the time components are sourced, to manufacturing through the channel and to the datacenter. This can certainly be a challenge. The news is filled attack of some sort on the supply chain – from modified BIOS to chip clipping incidents.
IT is understandably none the wiser to some of these hacks. As an ex-IT professional, I made the reasonable assumption that the servers landing on my loading dock from a very reputable vendor were free of tampering. But, it’s a different world with a diverse threat landscape, and these assumptions can no longer be made.
HPE addresses these concerns in a couple of ways. First, its Trusted Computing Group (TCG) Platform Certificates implementation makes sure that the components that populate a server at boot are the very same components that populated the server when it left the factory floor. Secondly, the company uses a Trusted Platform Module (TPM) to authenticate the Integrated Lights Out (iLO) management controller through a product cryptographic identity (IDevID). I cover HPE’s implementation of both Platform Certificates and IDevID in greater detail in a research brief which can be found here. Without these critical first steps in securing infrastructure, zero trust can never indeed be achieved.
Here’s why I like what HPE is doing
If you haven’t figured it out yet, cybersecurity is challenging. Securing the environment, workloads and data requires depth and breadth of prevention measures. HPE seems to look at security as an effort that extends throughout the lifecycle of the server. Frankly – even before the server is even manufactured.
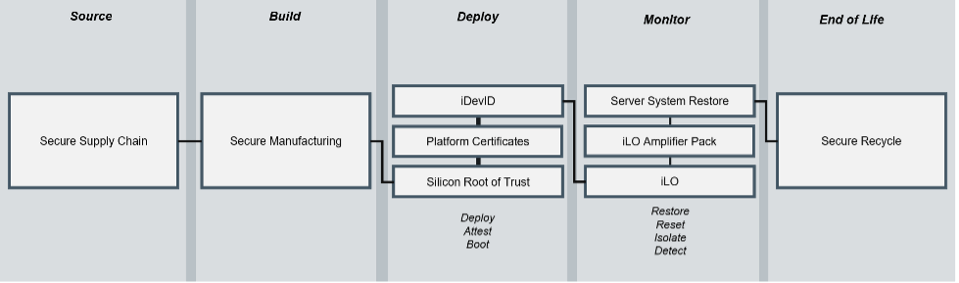
If you look at the above graphic, we look at the different phases of a server’s lifecycle – from sourcing raw materials to the secure recycling of storage devices and the like as a server is retired. Throughout this process, HPE has a corresponding solution designed to protect a company’s infrastructure and data. Note that these solutions aren’t just extended throughout the lifecycle—there is overlap through each phase. This overlapping nature of security assures hackers can exploit no gaps.
The above solution does not consider the recently announced Project Aurora. This initiative drives zero trust from the silicon through the workloads and data – from the core datacenter to the edge to the cloud. For more on that, you can read the research brief found here.
HPE has told a good story as it relates to security, dating back to the launch of its ProLiant Gen10 portfolio in 2017. More importantly, the company has consistently executed against that strategy with a steady cadence of solutions to strengthen its security portfolio. It seems this is an area where the company is intent on developing differentiation in the market.
Closing thoughts
Cybersecurity is a top-of-mind consideration for every IT executive. It is a continually evolving topic and a topic where failure can severely damage a company’s standing.
While a lot of budget is spent on cybersecurity solutions such as identity management and privileged access management, assumptions can sometimes be made about the security of the infrastructure deployed in the datacenter, the edge, and the co-lo facility.
It would be wise to look at what is being deployed and ensure you have the appropriate security measures in place, whether that infrastructure comes from HPE, Dell, Lenovo, Cisco or any other IT solutions vendor. It’s better to take the extra steps today instead of paying some Russian hackers tomorrow.
[/vc_column_text][penci_authors_box_2 style_block_title=”style-title-4″ columns=”column-1″ post_desc_length=”100″ number=”2″ order_by=”user_registered” include=”213″ block_title_fonts=”font_family:lato-regular%3Aregular|font_style:600%20medium%3A600%3Anormal” css_animation=”bounceInUp” hide_posts_url=”true” block_id=”penci_authors_box_2-1600361320259″ custom_markup_1=””][/vc_column][/vc_row]



